An Effective Protective Intelligence Investigation: Unraveling the Michigan Plot

- Protection personnel rarely see a roadmap into a plot to kidnap or kill.
- The aspirational plot to kidnap the governors of Michigan and Virginia shed light on pre-operational activities that are instructive for protection personnel.
- While many plots are disrupted by law enforcement authorities, protection professionals must use the lessons learned in these cases to protect against threats that may not be as visible to the authorities.
In October 2020, thirteen men were arrested and charged with plotting to kidnap Michigan Governor Gretchen Whitmer. The cell also looked at targeting law enforcement personnel, plotted civil unrest, and discussed attacking the State Capitol of Michigan, while later information indicated the group also considered targeting Virginia Governor Ralph Northam. One of the arrested suspects was a former Marine who worked for a security company. (source: Detroit Free Press) Fortunately, the FBI had infiltrated the group based on its earlier threats against law enforcement personnel and were monitoring their attack plans.
Even though the plot was more aspirational than operational, the case is very instructive for those of us engaged in the tradecraft of protection. As a student of protection history, I can’t recall another case in which two state governors were targeted for kidnapping. That in itself is unique. In fact, the case is a textbook example of an effective protective intelligence investigation. (source: Reuters)
Looking at the information available about the case, there are a few key takeaways that protection professionals should understand and build into their programs.
1. Pre-Operational Surveillance is Only Visible If You’re Watching
Tradecraft wise, the pre-operational surveillance actions have always been key in my mind in stopping the attack cycle. This cell was operational when they conducted reconnaissance of the Michigan governor’s summer residence. The question for me as I think about this plot is whether or not the protective details and police would have observed the surveillance actions of those involved in the plot, absent the intelligence developed by the FBI?
Surveillance detection works if you know what you are looking for, aided by training and technology tools. It’s the most cost-efficient manner of protection in the industry, as far as I’m concerned. If you don’t have a surveillance detection program in place, this plot is a reminder of the importance. (Learn more about surveillance detection exercises here.)
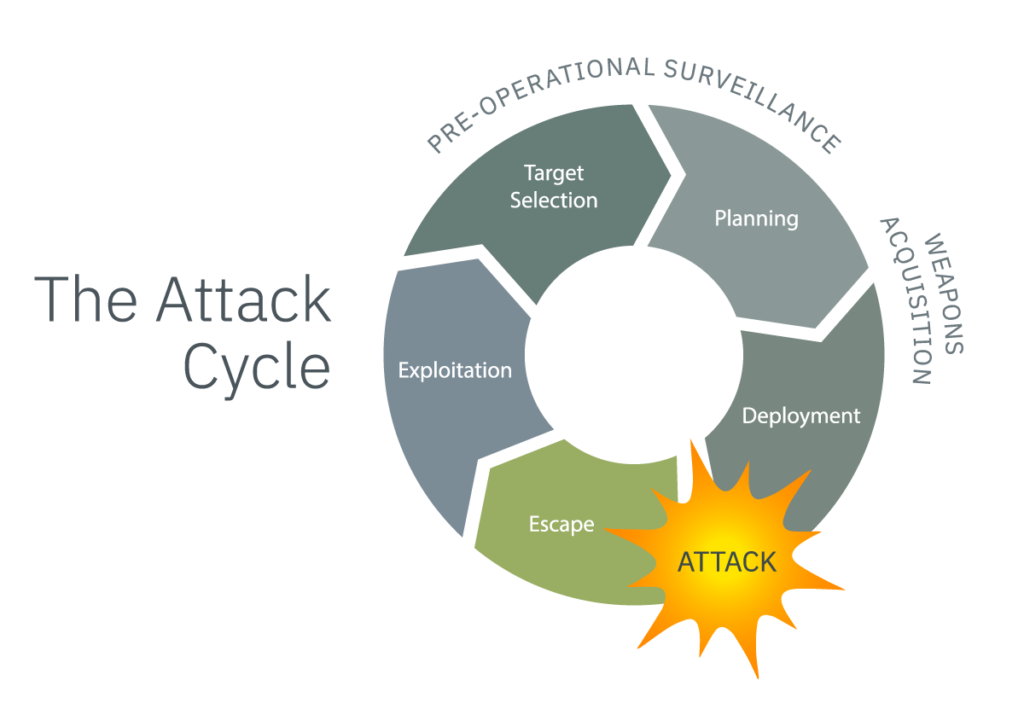 Technology can also be utilized to help your team watch for and evaluate potential threats. In this plot, the affidavit says members of the group drove by the Michigan governor’s residence in Lansing and her vacation homes numerous times, while also conducting surveillance by boat from the waters near her vacation home. Technology, such as license plate readers, can be used to identify unusual vehicles near the protectee, while robust databasing and analysis capabilities can help to determine whether these passes are unusual or coincidental.
Technology can also be utilized to help your team watch for and evaluate potential threats. In this plot, the affidavit says members of the group drove by the Michigan governor’s residence in Lansing and her vacation homes numerous times, while also conducting surveillance by boat from the waters near her vacation home. Technology, such as license plate readers, can be used to identify unusual vehicles near the protectee, while robust databasing and analysis capabilities can help to determine whether these passes are unusual or coincidental.
2. Attackers Understand When and Where Your Protectee is Most Vulnerable
Even though this group of attackers was largely aspirational, their framework for conducting surveillance was sound. It provided substantial details about Governor Whitmer’s activities and the best locations for a potential attack. According to the affidavit, the group had decided that, based on their surveillance activities, “their best opportunity to abduct Governor Whitmer would be when she was arriving at, or leaving, either her personal vacation home or the Governor’s official summer residence.”
There are two dangerous aspects of this issue to consider:
- First, the group was very cognizant of the times when the governor would be most vulnerable to an attack, and they built their plans to coincide with the most critical times.
- Second, they understood that security measures may be more lax at a vacation home compared to the normal work environment. They made plans on that basis, raising the chances for a successful kidnapping operation.
In this business, vacations and off-duty hours pose unique protective security challenges for protection details. This is especially true for VIPs who are seeking to have less security than they would in their normal work and home environment. This case is a vivid reminder of why threat assessments need to be constantly evaluated. Just because a protectee is on vacation doesn’t mean that the threat has diminished. On the contrary, that’s the time any good (or even bad) surveillance team would see that security has been reduced.
3. Attackers Are Planning For Secondary Attacks, You Should Too
One of the more interesting parts of the bigger-picture analysis of this plot was the group’s plans to attack secondary locations to slow down first responders, reportedly including plans to blow up a nearby bridge or throw molotov cocktails into police vehicles. This was a novel idea and a reminder of something that is rarely looked at in threat assessments. Some questions to consider include:
- What are the response times in various locations for fire, police and EMS?
- What could slow down first responders?
- Is your team prepared to handle the initial fallout from a potential attack if first responders are delayed?
- Is there a safe haven in the vacation home?
- Do you have a trauma kit and Stop The Bleed supplies?
In this case, the plotters were infiltrated by the FBI who was relentlessly monitoring their activities and stopped the group before it took action. For protection professionals, it’s critical to ensure your team is taking appropriate action to find surveillance, use technology where possible to support your efforts, maintain appropriate security measures in all areas, and reevaluate your response plans for any attacks that might not be spotted by law enforcement in time.
Ontic can help businesses like yours stay safe and avoid unfortunate events, such as what occurred in Michigan. Learn how our team of experts can help optimize your security program at Ontic’s Center for Connected Intelligence.




