Gaining Deeper Insights Beyond Social Media Threat Intelligence

When we zoom out and think about corporate threat assessment investigations holistically, it’s clear that social media threat intelligence plays a significant role — but how significant is it?
In this article, we’d like to explore the benefits of using social media threat monitoring when conducting investigative research, as well as the pitfalls of relying solely on social media to manage threats.
There are four clear advantages to timely social media threat assessment:
01
BREAKING NEWS ALERTS
Social networks are a useful tool for real-time event alerting. It’s no secret that news often breaks faster on various forums long before it hits cable or local news.
02
SOCIAL LISTENING FOR KEYWORDS
Social media and related social listening tools are an excellent way to gather data and get alerted to attention-grabbing keywords such as the name of your asset in close proximity to threat terms. Early data collection and notification of potential threats via social media posts and comments that need to be triaged and assessed are essential for brand protection, and social media is quite useful in this respect.
03
RECOGNIZING ESCALATING TRENDS
Important insights can be gained about threat actors via online trends they engage in. This gives security professionals the supporting details they need to make informed social media threat assessments about the nature of a threat.
04
NETWORK ANALYSIS
Although social media carries with it many unknown factors such as who is actually behind a given account, it can provide investigators with a web of connections to be mapped via data analysis tools used outside of social platforms.
Generally, social media can be useful for identifying threats quickly. It helps surface anomalies that need to be investigated, then the analyst is able to triage them and make quick assessments from there. And for the most part, that’s where the role of social media ends (minus ongoing monitoring of keywords).
Now, what risks do we run in limiting our investigations to social media threats alone?
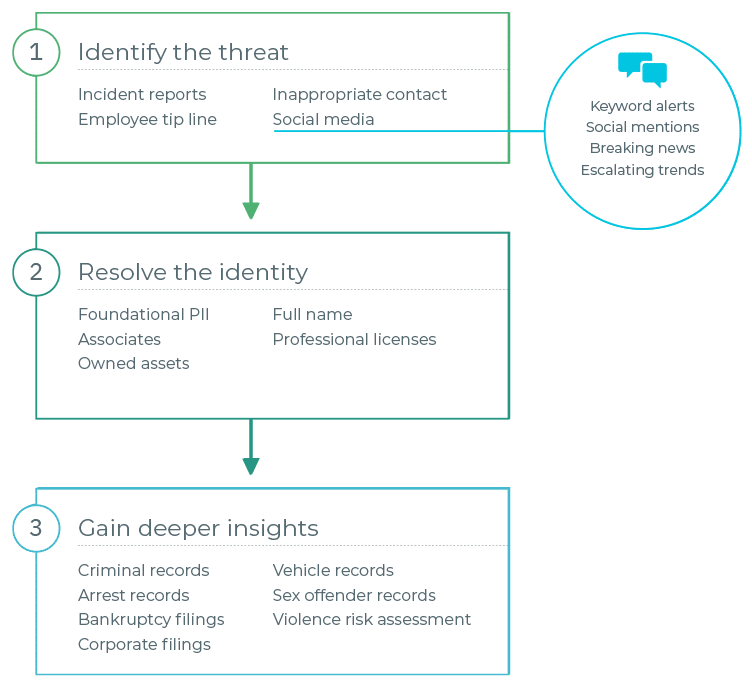
Identifying the person behind the threat
Using social media alone limits an analyst’s ability to identify the person behind the threat. What’s more, analysts must be cognizant that they are not violating terms of service when monitoring social media platforms. After identifying potential threats on social media, the next logical step is to resolve the identity of the person behind it, which will help the investigator assess the threat.
Oftentimes, resolving the identity of the person behind an online profile with a high degree of certainty requires the use of credentialed investigative data sources such as TLO, Accurint, LexisNexis, etc. Social media alone is not a reliable means of identifying the human behind an online threat — as many here have experienced, it’s easy to find yourself going down a rabbit hole of information on the wrong person when using social media on its own.
Gaining deeper insights to see beyond the surface
It is critical to see beyond the surface of the investigation, prompting the need for deeper insights that are unavailable via social media threat detection alone. After using credentialed data sources to resolve the identity of the threat actor, the investigator can take what they learned (e.g. foundational PII, professional licenses, asset ownership, associates, etc.) and dive deeper into additional sources to identify physical and digital risk factors that help the investigator understand the threat actor’s behaviors, motivations, and capabilities.
The many pieces of information from credentialed data sources and social media investigation tools give the investigator hints as to what additional sources they should check and where they are likely to find useful information.
For example, the threat actor’s address history tells the investigator where to search for county/state civil & criminal records, sex offender registries, property records, Secretary of State filings, vehicle registrations, etc. Or a security guard license through BSIS might indicate firearms ownership. There are many ways that information from credentialed sources support investigators’ discovery of deep insights.
Final Thoughts
While this is only a brief overview of the role that social media plays in the wider investigative process, it clearly demonstrates that social media threat intelligence is a small piece of the overall investigative process. It is beneficial for the identification of potential social media cyber threats — however, it begins to lose value as investigators move onto identity resolution and the collection of deep insights relating to threat actors.







