Who We Serve
Today’s top brands are upgrading security with Ontic
Do you need a partner in advancing your security program? Join a community of 20,000+ professionals striving to secure organizations of all sizes — and who trust Ontic as a software provider and industry leader.
Discover real-world success stories
Ontic is a force multiplier that helps security teams get proactive, deliver more favorable outcomes, and measure performance.
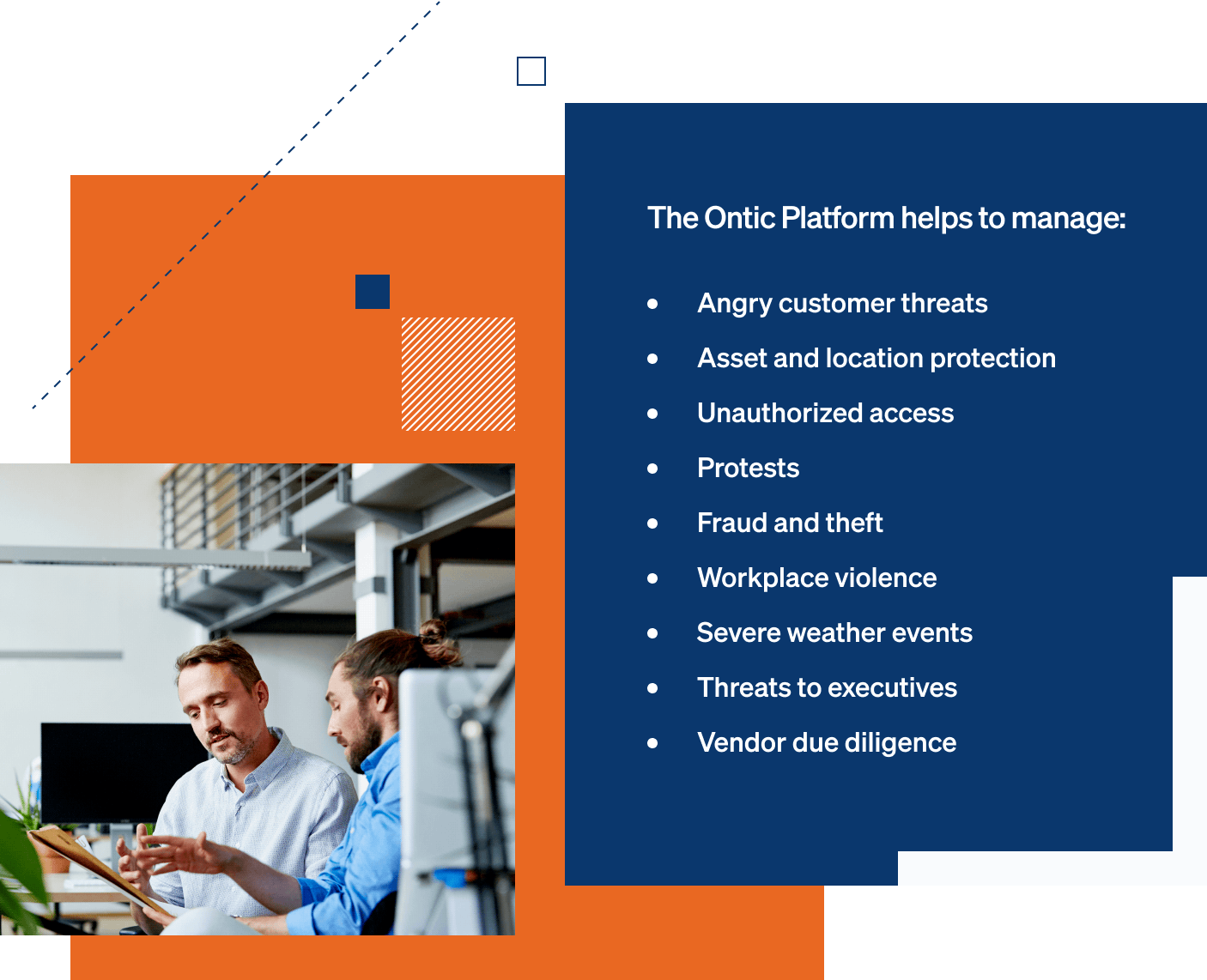
Common Challenges
We’ve supported our clients through it all
Regardless of the industry, Ontic helps security teams improve effectiveness and find new efficiencies with Connected Intelligence. Holistic, real-time data plus streamlined workflows deliver measurable performance.
Why We Serve
Security best practices are business best practices
A good security program keeps people safer and makes businesses stronger. Rather than a tactical cost, we help businesses see security as a strategic imperative. With Ontic, security teams not only protect assets, they inform sound business strategy.
Our clients know that:
US employees do not feel safe on the job
in annual losses are attributed to workplace violence
of today’s execs worry that current risk policies cannot meet future needs
US employees experience workplace violence in an 8-week period
more costly to handle workplace violence than to prevent it
lower security opps costs with
software-powered programs
Serving intelligence and solving challenges across industries
Ontic brings security practitioners across a wide range of industries together, sharing best practices as business threats evolve. Whatever your industry, our purpose-built security software helps teams like yours work smarter and move faster.
Work smarter, faster, and better with Ontic
What’s your top challenge? No matter what your security responsibilities are, our purpose-built software delivers the Connected Intelligence your team needs to succeed.