The Enemy of My Enemy is My Friend: The Unification of the CSO and CISO
Don’t be surprised by what can be accomplished when a CSO and CISO join forces to mitigate insider risk
What Does a Collaborative Approach Look Like?
How to Define an Insider Threat
Pre-Incident Indicators of Compromise
The Common Insider Incident Investigation Scenario
Whether you are fighting anonymous digital adversaries or those that operate in the flesh, it’s fair to say that in our security landscape, insider incidents rank high on the list of public enemies. One of our advisors once said that cyber teams use bits to protect bits, while physical security teams use bits to protect atoms. This is mostly true, although a lot of bodies are still required to protect physical infrastructure. For those of you about to gloss over at this point, hang with us, as I promise this is germane to the physical security intelligence practitioner.
The differences in the application of tradecraft by both cyber and physical teams are enormous. If you were to research the history of insider risk and related mitigation techniques, one would assume that insider risk is strictly a cyber problem that can only be solved by cybersecurity teams, using their dedicated strategies and tools. After all, cyber seems to be well regarded as a safe and necessary investment, and it requires less scrutiny to obtain a realistic operating budget.
In retrospect, physical security teams are often viewed as cumbersome, slow-moving, and highly reactive cost centers. They are not typically recognized as invaluable C-Suite resources who are instrumental to the overall business success of the enterprise. Cyber and physical security teams remain extremely siloed by nature, and who can blame them? They define risk differently and view the threat landscape through a completely different lens. The teams also speak a different language and mitigate risk in an entirely different way.
Many people continue to assume that the insider risk topic has been thoroughly vetted & defined and that a consensus has been reached regarding the best solutions for the problem. As you dig deeper and seek feedback from security professionals, it becomes clear that the interpretation of insider risk varies across security teams, and depending on who you ask, mitigation strategies also vary greatly.
How do we unify the approach?
In all my years of conducting physical threat and vulnerability risk assessments, I have yet to see a fully unified cyber and physical security team. While the general perception continues to reinforce the rumor that cyber owns insider risk mitigation, we are seeing an interesting evolution occur right before our eyes, where CSOs and their supporting intelligence teams are not only joining in but, in some cases, leading the fight against insider threats.
How did this occur? First, remember that when protecting a business from insider risk, you aren’t just dealing with digital assets, networks, servers, and firewalls. You have much more to protect, including vast amounts of physical infrastructure, including decentralized workforces, workplaces, intellectual property, supply chain, and all of their supporting cast members. To protect this vast network of physical assets, it’s important that you’re looking in the right places for elevated risk. This involves monitoring access points and extended vulnerabilities that are created by humans — on-site and remote employees, vendors, contractors, and even those that are in the circle of influence of our customers. Much of the additional context can only be provided by monitoring and detecting three-dimensional human behavior in action.
I previously addressed how a cyber attack starts off as an exploited physical vulnerability, and physical attacks are rooted in cyber vulnerabilities. Defending against an insider incident is much more than simply waiting for an alert from a Security Information Event Management (SIEM) platform. Although those systems will continue to remain critically necessary, many insider issues are detected because an employee or contractor circumvented physical infrastructure in the planning stages prior to a malicious act. That is why you need to use comprehensive intelligence monitoring techniques to help recognize threats well before they become critical situations — because, at the root of this, a human somewhere is part of the planning and attack cycle.
To fight this battle effectively, both cyber and physical security teams must join forces and agree on the most appropriate strategy for their organization. Remember, most of the required data, tools, and security leaders already exist in your company today. So we must ask ourselves:
Why is widespread collaboration between CSOs and CISOs not yet evolving on a broader scale – especially when we know that many insider threats are initially detected via physical security monitoring as well? And what does collaboration actually look like in real life?
When analyzing many of the more notable incidents that impact the supply chain, workplace security, and other critical infrastructure, I’ve noted that insider risks are often hybrid in nature, meaning that they are initially detected as a digital signal or alert via a cyber monitoring system, yet have a significant nexus to physical infrastructure. Due to the nature in which the threats are planned for and carried out, many have physical risk indicators, which makes them detectable by systems that recognize human threat actor behavior.
This is why a proper physical threat-hunting program must complement and interface with your digital threat-hunting operations. Cyber threat hunting is key, yet it alone will not allow your teams to understand the bigger picture of the risk landscape nor take the most appropriate action.
So with the increased frequency of these types of insider incidents, the question remains: Why is this collaboration between the CSO and CISO not yet evolving on a much broader scale?
We often notice that while cyber and physical teams have vastly different tactical objectives, their strategic goals remain the same, which is to reduce risk and liability to the company, its assets, and of course, its people. For more insight on this question, Josh Massey, Department Manager at MITRE, provides his point of view.

“The malicious actor does not think in terms of cyber versus physical, so why should security defenders? Rather, a motivated and malicious actor will follow the path of least resistance toward the desired target. This means a ‘hard’ physical target naturally funnels the adversary to the ‘soft’’ cyber target (or vice versa). In essence, ‘my success is your demise’. Unfortunately, siloed security practices such as this lead to a zero-sum game where one can still claim success despite others’ failure. However, a more collective approach would view the problem as we either win together or lose together. At MITRE, we’ve structured our insider threat program to eliminate the artificial, functional turf wars of security silos in favor of an enterprise security risk management (ESRM) approach which emphasizes risk principles (vs functional competencies) to managing security risks.“
Josh Massey, Department Manager at MITRE
According to Brian Allen, an ESRM evangelist, “When ESRM principles are applied, the security function changes completely — from a set of tasks, performed discretely, to a role. ERSM means security decisions are made by the right person, with the right authority and accountability, and for the right reasons — reasons based on defined risk principles.”
What does a collaborative approach look like?
To adequately describe a proactive insider risk solution based on the cooperation of both physical and cyber teams, you first need to establish a foundational understanding of who insiders are, what an insider risk is defined as, and lastly, which pre-incident indicators of insider risk are most detectable. For this, I will reference baseline definitions provided by the United States Cyber & Infrastructure Security Agency (CISA).
Who are insiders?
According to the CISA, insiders are described as any person who has or previously had authorized access to or knowledge of an organization’s resources, including personnel, facilities, information, equipment, and systems. Examples of an insider include the following:
- A person the organization trusts, including employees and those to whom the organization has given sensitive information and access.
- A person is given a badge or access device identifying them as someone with regular or continuous access.
- A person to whom the organization has supplied a computer and/or network access.
- A person who develops the organization’s products and services.
- A person who is knowledgeable about the organization’s business strategy and goals, entrusted with future plans, or the means to sustain the organization.
- In the context of government functions, the insider can be a person with access to protected information, which, if compromised, could cause damage to national security and public safety.
How to define an insider threat
TheCybersecurity and Infrastructure Security Agency (CISA) defines insider threat as “the threat that an insider will use their authorized access, wittingly or unwittingly, to do harm to the department’s mission, resources, personnel, facilities, information, equipment, networks, or systems.” This threat can manifest as damage through the following behaviors:
- Espionage
- Workplace violence
- Terrorism
- Sabotage & unauthorized disclosure of sensitive information
- Intentional or unintentional loss or degradation of departmental resources or capabilities
- Corruption, including participation in transnational organized crime
Pre-incident indicators of compromise
Lastly, let’s describe some of the most notable pre-incident indicators or detectable symptoms of insider risk. In his book “Beyond Fear,” security expert Bruce Schneier discusses the motivations and behaviors of malicious insiders. Schneier reminds us that detecting a malicious insider attack can be extremely difficult, particularly when you’re dealing with a calculated attacker or a disgruntled employee who knows a great deal about your company. One way to detect such an attack is to pay attention to the various indicators of suspicious behavior, which include both digital and physical indicators, some of which are listed below:
- Poor performance appraisals
- Voicing disagreement with internal policies
- Disagreement with coworkers
- Financial distress or unexplained financial gain
- Unexplained travel patterns
- Odd working hours or a hasty departure from the company
- Attempting to access restricted areas of the company network
- Data offloads
- Failure to complete mandatory security training
The common insider incident investigation scenario
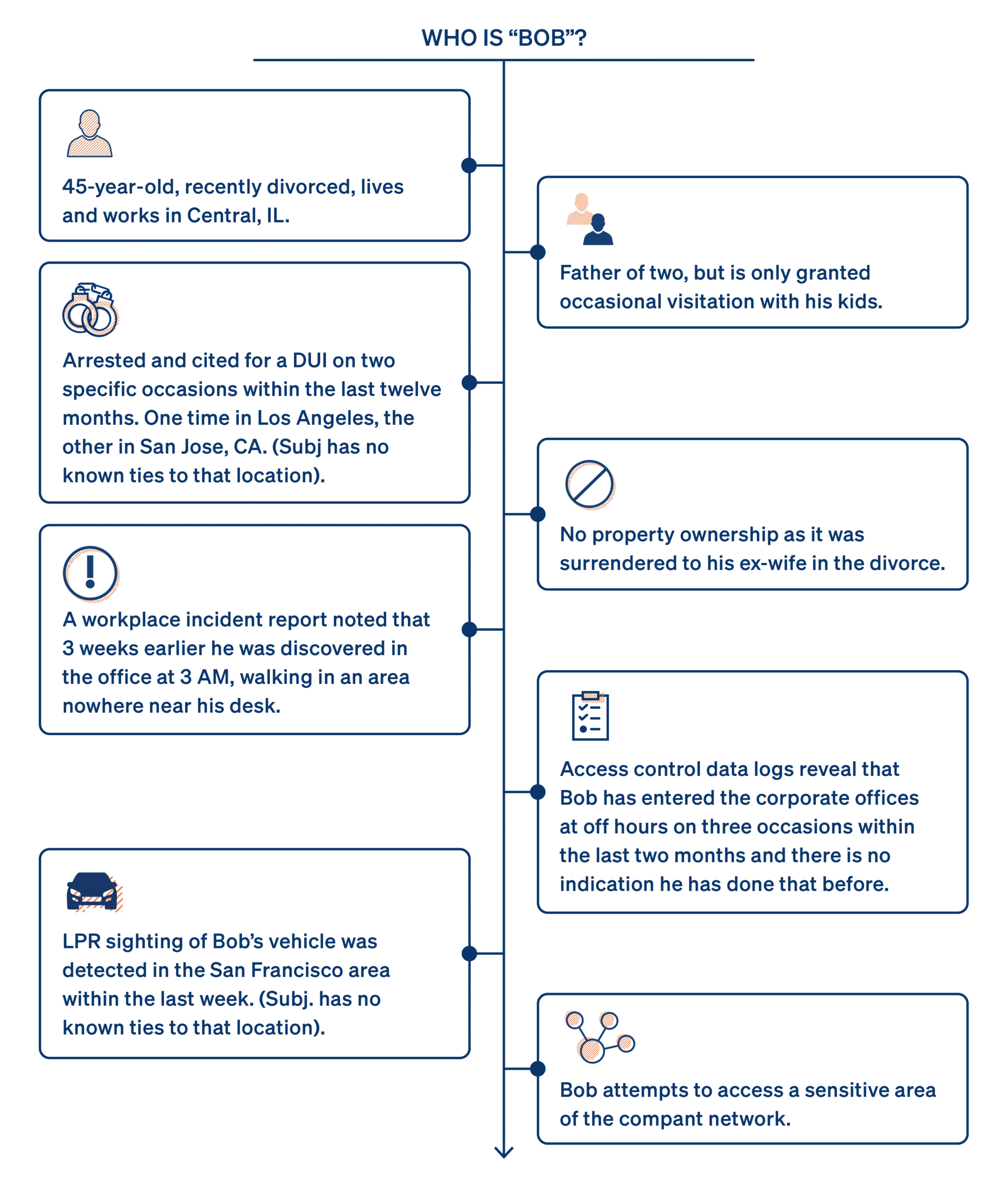
Now that we have a roughly defined baseline, let’s play out a typical scenario with the actual data, tools, and techniques we have available today, using a collaborative approach. In the following insider risk use case, it is noticed via a user activity monitoring system that an employee (Bob) repeatedly attempts to gain access to a restricted part of the corporate network. In order to gain the best intelligence, you need participation from the right people with the right mindset, implementation of a unified process, and adoption of appropriate supporting technology.
Determine if the individual is a credible threat to the business. To accomplish this at scale, kick off a workflow that will allow you to discover other pre-incident indicators so you can add context to the indicators of compromise that triggered the concern in the first place. As you cultivate that intelligence, you need to properly assess if this person was just having a bad day or are they fit the known behavioral patterns of a malicious insider.
A typical genesis of a SIEM alert
A Security Information and Event Management (SIEM) alert is a notification that your SIEM system generates to indicate a potential security threat or event. Let’s use an example to illustrate the genesis of a SIEM alert. You receive a notification that Bob recently attempted to access a compartmentalized part of the network he once had access to for a special project. It appears that Bob used two-factor authentication when attempting to access the network multiple times, from the company IP address. Corporate access control data shows that Bob was in the building at the time of the incident. So now what?
Bob is interviewed and mentioned that he just needed to get a file to reference for a prior project. If you are satisfied with the answer, that’s where the investigation could possibly end. This might be something you have seen many times. But as you uplevel your threat-hunting game, you want to see what the proper convergence of cyber and physical data could tell you.
The insider incident investigation workflow referenced below is relatively similar to the one Ontic covered in the Guide to Establishing an Intelligence Baseline. This one, however, will require deeper access to your company’s legacy data and a greater level of participation from the right teams to successfully implement. As with the workflow in the guide, these are suggestive outcomes you are looking for, not prescriptive steps. Remember that all teams have varying work styles and take that into account when moving through the following workflow:
01
Resolve the identity of the potential threat actor
This is typically much easier to do with an insider case as external actors operate in the shadows. It’s still important to ensure that you’re tracking the right individual (or individuals) so that a proper investigation can be conducted. If you fail to consider that an individual has multiple identities, uses a subtle alias, maiden name, etc., your investigative results may be skewed, and the bigger picture may be missed.
02
Scan company systems for internal data
This is where full cooperation from physical, cyber, legal, and HR will transform your results. This means checking all known incident reports, investigations, and observations, as well as data logs of access control systems, including license plate readers, arrest record feeds, and other systems of record, to see if there have been any issues associated with this employee in the past. You are looking for anything indicating that the person was involved in a hostile interaction while on company property, attempted to access the corporate facility off hours, had behavioral issues, or other risk indicators. This data is critical and it is most likely already stored in your company somewhere. Having access to it will allow the analyst to know quickly if this is a net new issue or a critical indicator of a newly discovered threat.
03
Public records and OSINT
This is the area that seems to be under-leveraged or misunderstood. To benefit from the value of this information, the right approach to OSINT and public records needs to be coordinated. I promise that it’s as important as any other step in this workflow. It’s inexpensive, it can be driven with standard operating procedures so it is highly scalable and somewhat automated, and it may generate a wealth of information related to the background of the person of concern. You want to know about civil litigation records, criminal history, and financial-related cases such as collections issues, bankruptcy, liens, judgments — even evictions and foreclosures. You want to see if there is a potential motivator for financial gain or other ongoing issues that may incentivize or trigger malicious behavior. Additionally, with a proper OSINT scrub to include an adverse media search, you can determine a person’s mindset, mode of living, and affiliated interest groups and determine what their standard behavior looks like.
04
Initiate an investigative assessment
It’s important to collect the right information and quickly discover anomalies or other concerning patterns. You’re looking to see if any original incidents of concern now appear more serious or can be explained away by other factors. Just as there are assessments geared towards workplace violence, there are also formalized insider threat assessment rubrics that can generate risk scores to determine the likelihood that someone is a potential risk for insider threat. This is an area that can generate the proper “what next” for the investigator and create broader defensibility for the organization.
05
Alert proper teams, gather and share intel
Work closely with other departments, including legal, HR, campus security, or even law enforcement, if deemed necessary. During this step, you are both cultivating more information that may lead to actionable intelligence and making others aware of what they need to know to shore up their infrastructure. There may be an overlapping issue that can be discovered if the proper teams communicate effectively. Just like the investigative workflow for determining pre-incident indicators of risk, this step can and should happen early and often in the investigative process. It does not have to happen in sequence with other steps.
06
Establish or recalibrate protective strategies
This is where the complete picture is analyzed, and the decision is made to either close out or escalate the investigation, implement in-depth monitoring, or even exploit the threat in order to determine if it’s associated with a larger party of threat actors. A lot of this will depend on legal constraints, company culture, and sensitivities, as well as the business’s acceptable level of risk.
Context is key
Successful investigations require art, science, and decades of experience, which include the development of a gut instinct to keep running down a lead. No checklist can replace that, and we would never attempt to over-standardize a process as sensitive as this. But as we demonstrate a connected workflow where the right people can quickly generate the right information, imagine a scenario where the following information is what you find on the fictitious character Bob. Then ask yourself: How would the urgency heighten, and would your monitoring and mitigation strategy change?
Understanding the bigger picture
With a holistic threat detection approach, you can now layer in all pertinent information to more accurately understand the evolution of insider risk. Just like with physical risk indicators, you can uncover potential trigger events in a threat actor’s life (Like the anniversary of termination, a death in the family, or perhaps a tense legal case involving a divorce or financial issues). By surfacing this type of information and comparing it to the digital signals and indicators that cyber teams have access to, insider risk intelligence teams can more accurately determine the bigger picture and mitigate the threat quicker than ever.
As we continue to dissect the evolution of insider risk, it is evident that these investigations do not rely solely on cyber systems and tradecraft. Many physical intelligence teams uncover behaviors that allow us to recognize a pre-incident indicator of risk. These pre-incident indicators or indicators of compromise can be generated through human intel, incident reports, anomalous behavior in access control and visitor management systems, license plate readers, and data gleaned from continuous monitoring involving criminal activity. This is why collaboration between teams is so critical.
Is it overly idealistic to think that a CISO and CSO will join forces to mitigate insider risk? I don’t think so. I see the capabilities we have in front of us, and the culture shift is gaining momentum. As organizations start to tear down silos, they are getting a much broader picture of the insider risk landscape. Security intelligence and cyber teams are not locked in a zero-sum game. In fact, they have much to gain by collaborating because they face identical challenges, which are occasionally driven by identical threat actors. If we can work together to proactively identify, disrupt, and, most importantly, mitigate insider risks, we have achieved an important victory.







