Investigative Research
Turn vague leads into complete threat profiles
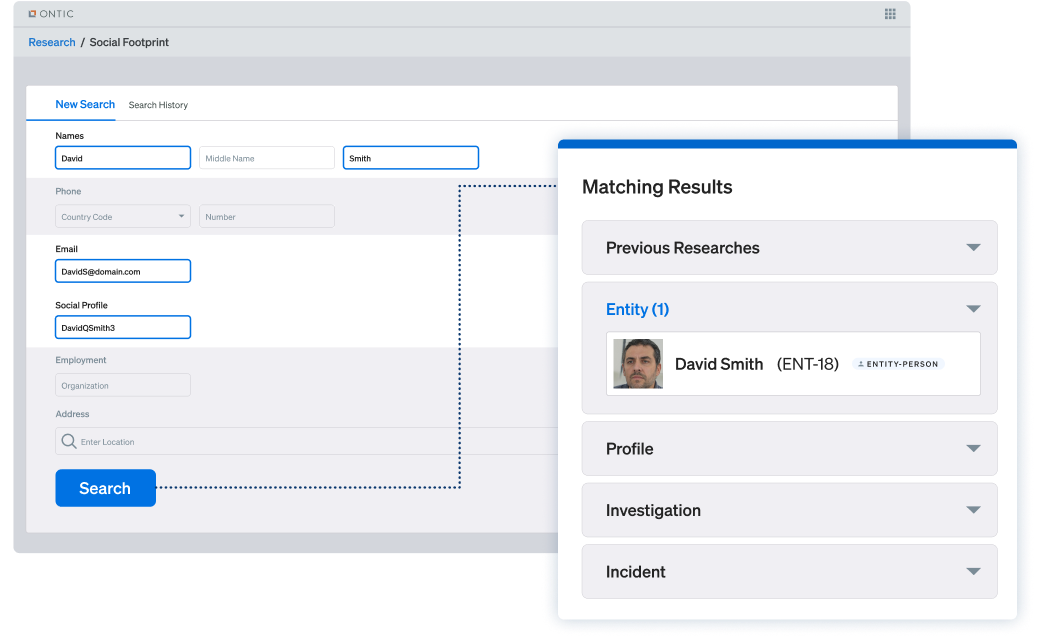
Most investigative research starts with fragments.
Replace 10+ research tools with one comprehensive research platform to uncover threats faster and monitor ongoing updates.
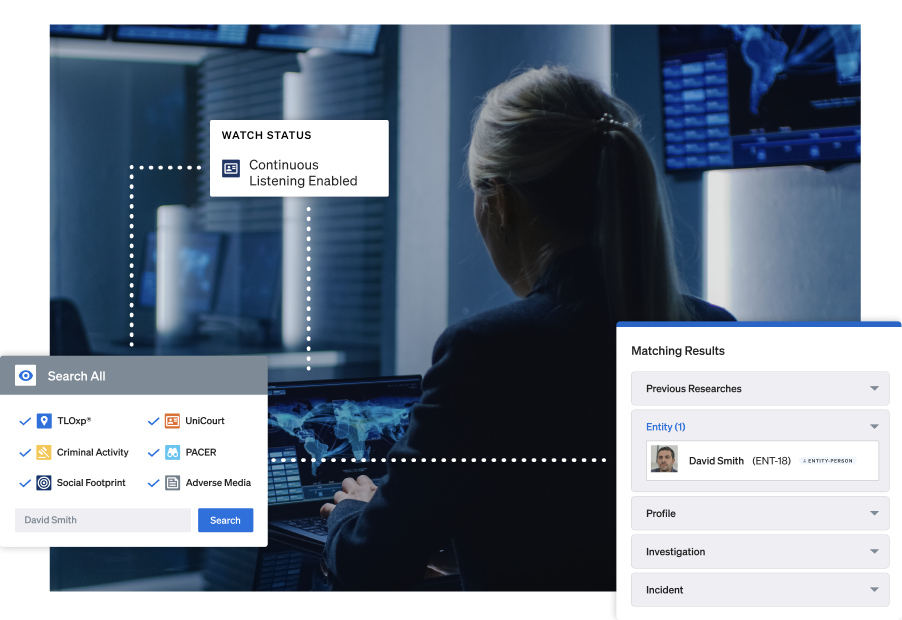
Investigate faster. Search smarter. Stay alert.
Cut research time by 50%
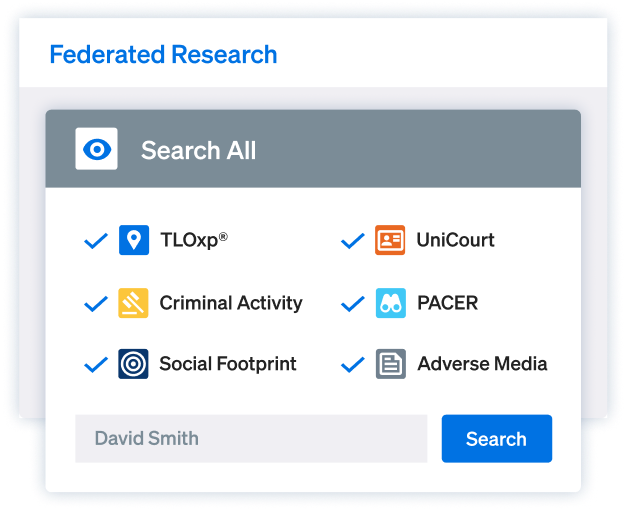
Ontic unifies your research tools in one place so you can move faster.
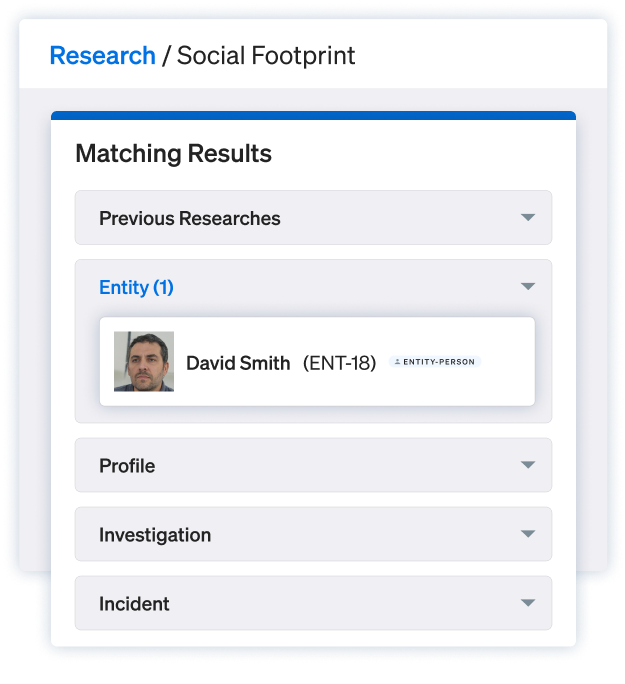
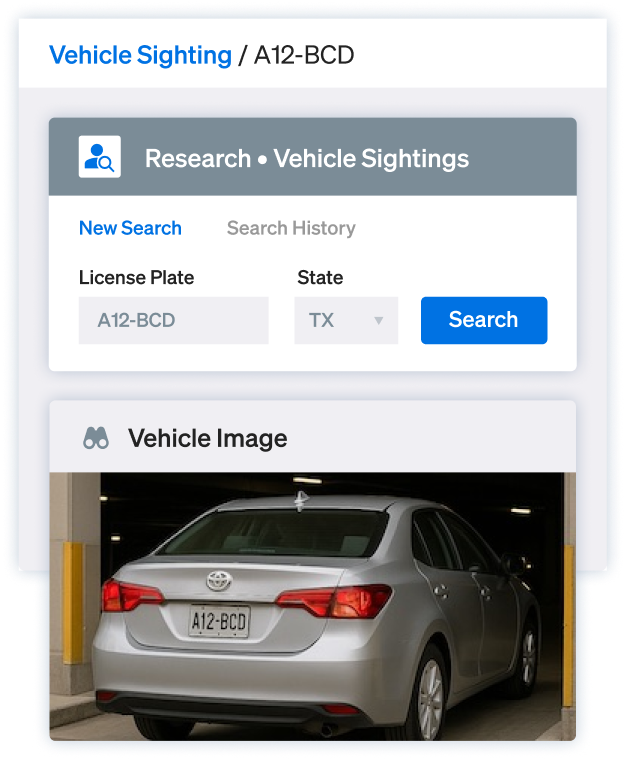
Search wider
Ontic connects identifiers across sources so you verify faster and act with certainty.
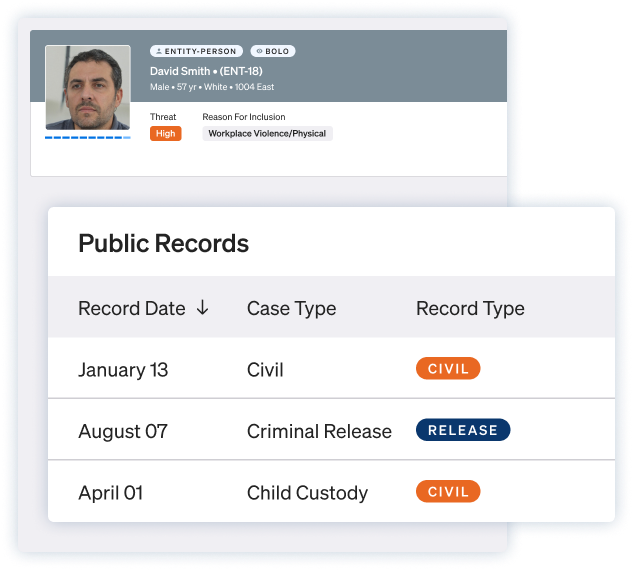
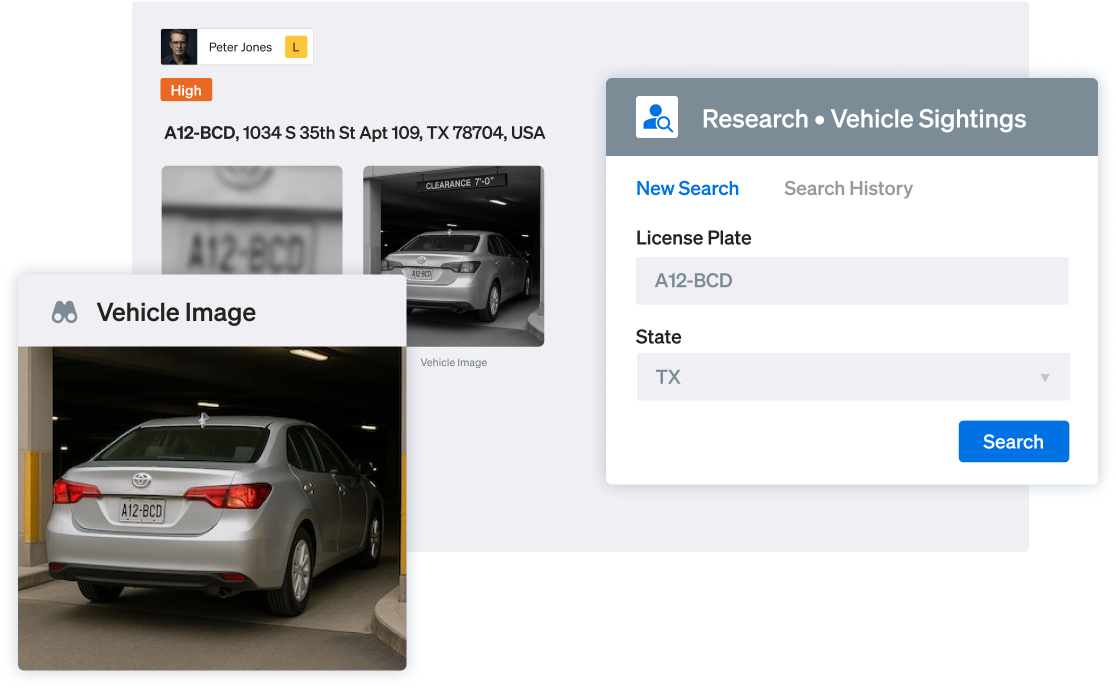
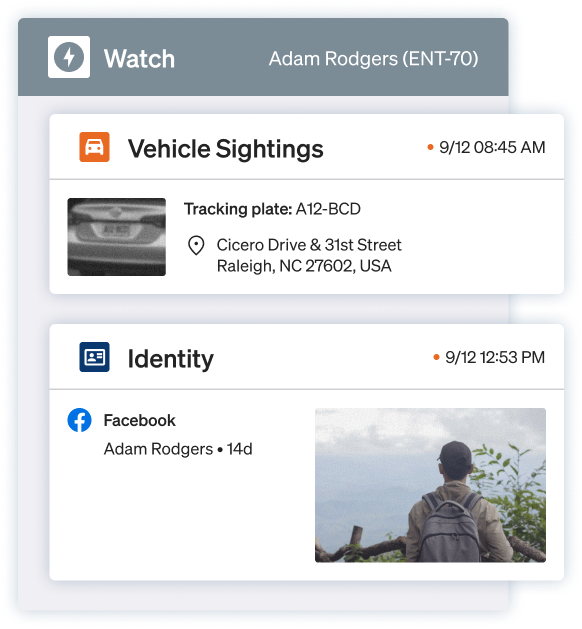
Automate monitoring
Ontic keeps watch — surfacing new arrests, sightings, or filings tied to known threats.
The Ontic Solution
Stop digging around
and start digging deeper
Ontic connects investigative research, monitoring, and reporting in one workflow so you can move quickly and stay ahead of emerging threats.
Platform
Centralize your data, cut the busywork, and get full context in one place.
Client Stories
Trusted by the people you trust
Trusted by thousands of security professionals at hundreds of leading brands. Ask around — chances are someone in your network already uses Ontic for investigative research.
Frequently Asked Questions
Integrated Research FAQ
Ontic is compliant with the highest security standards, trusted by leading security teams, and ready to handle what your program demands.
Ontic has Federal Risk and Authorization Management Program (FedRAMP) “In Process” status and is listed on the FedRAMP Marketplace.
Integrated Research Resources