Risk Assessment Software
Turn paper checklists into real risk reduction
Most risk programs still run on spreadsheets and emails.
Ontic digitizes assessments and vulnerability tracking so you can spot and fix issues before they escalate.

Assess risk. Resolve vulnerabilities. Justify budget.
Standardize
risk assessments
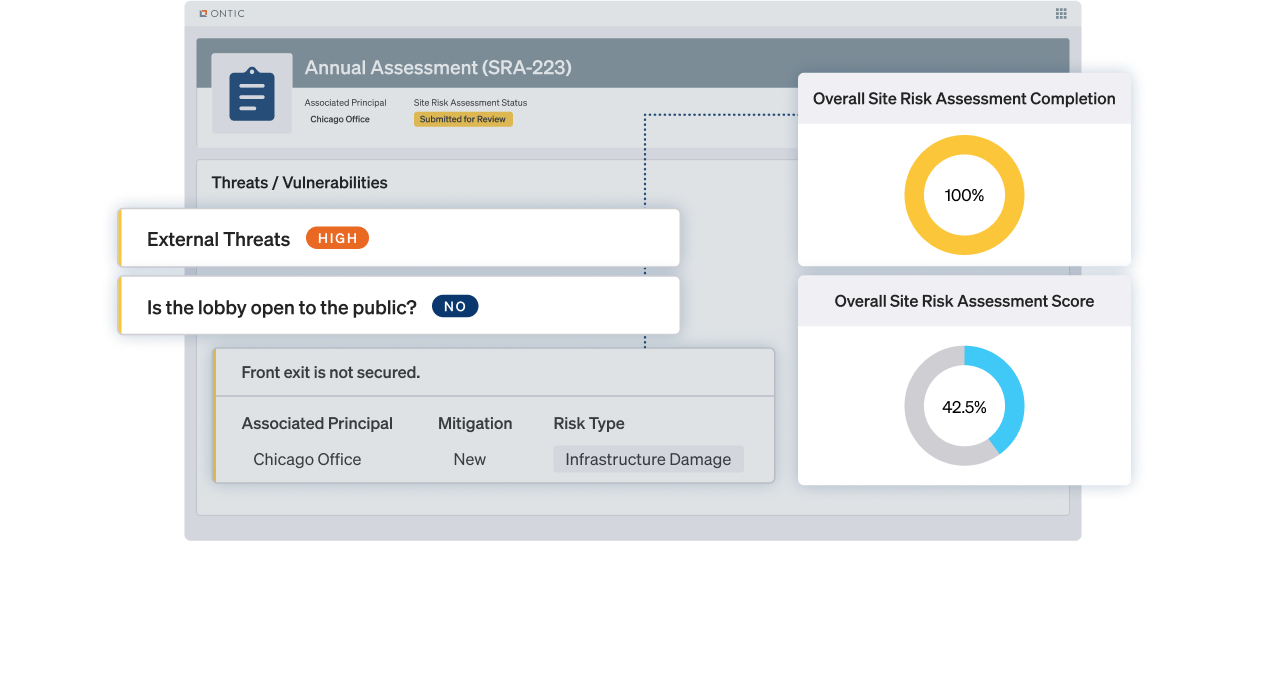
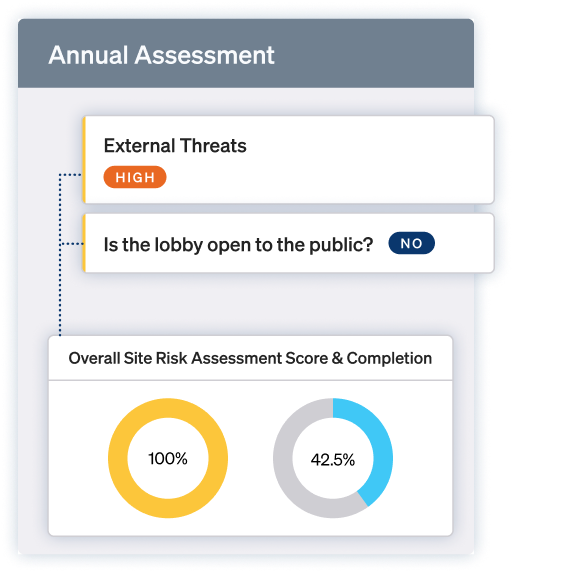
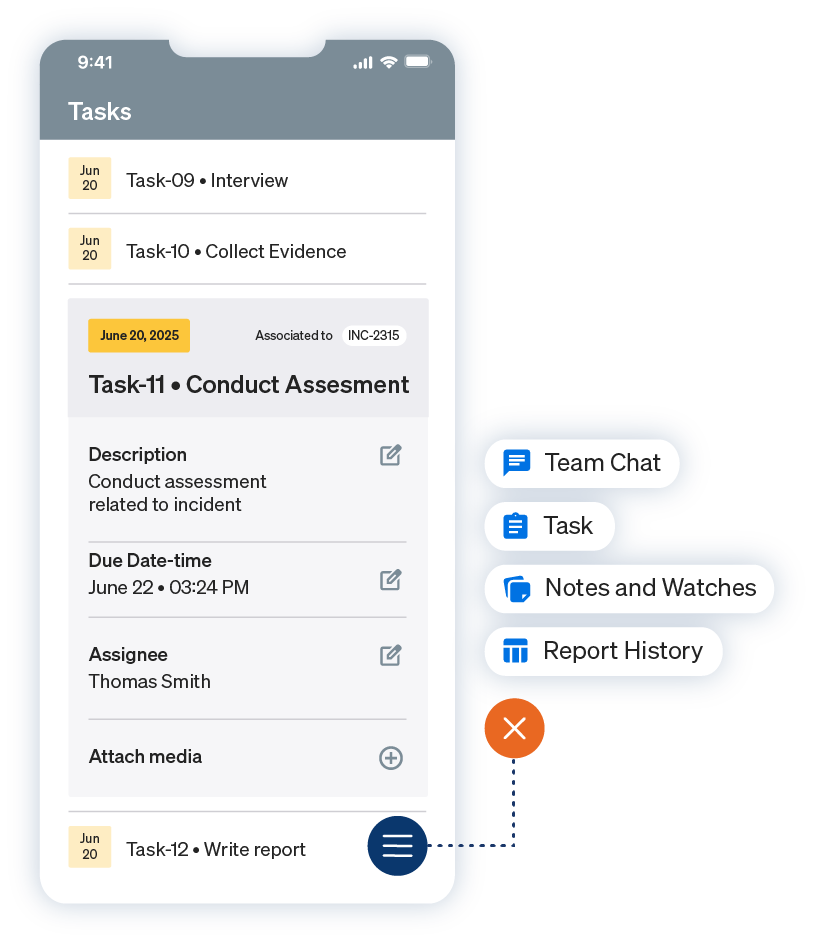
Design and deploy digital, repeatable assessments for every site and asset.
Manage vulnerabilities end-to-end
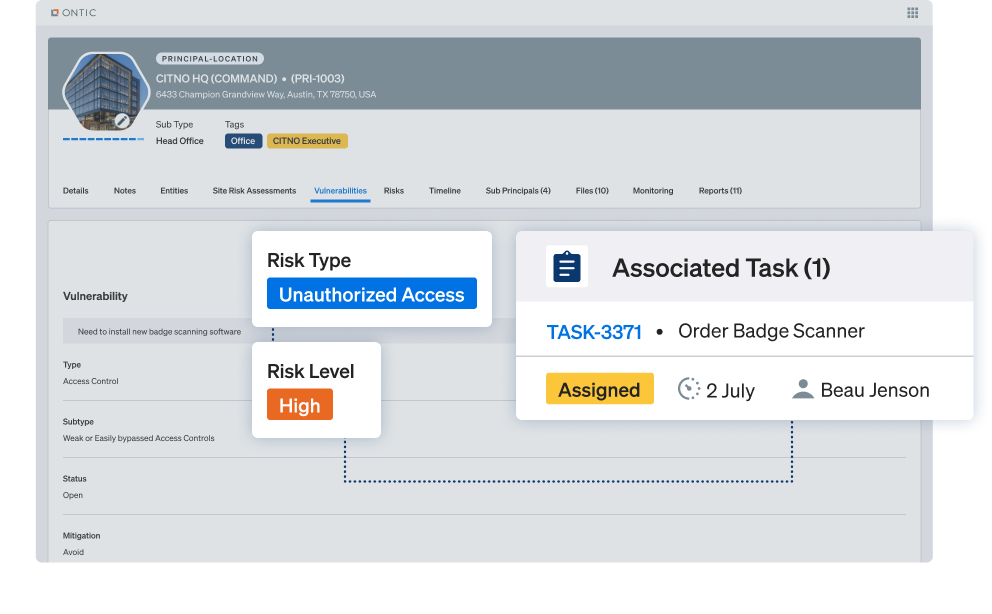
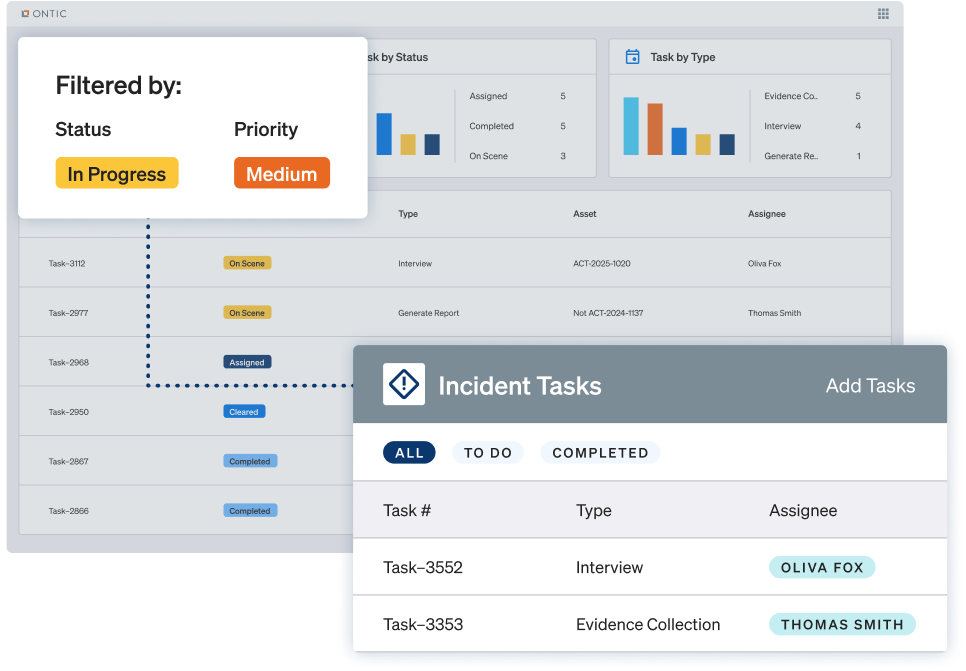
Track, prioritize, and resolve vulnerabilities from discovery to closure in one platform.
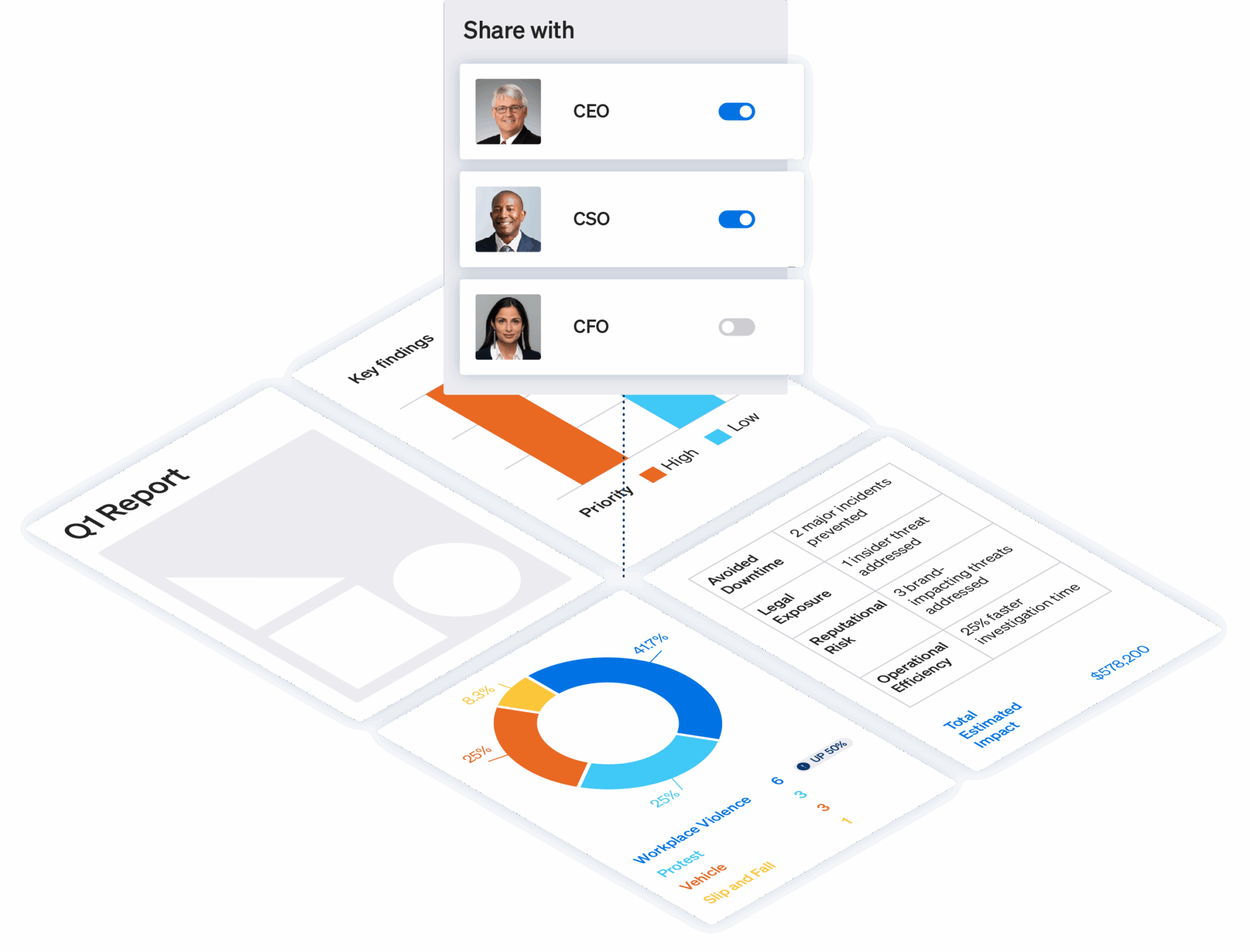
Make the case for budget
Share powerful reports that demonstrate progress, risks, and business impact.
The Ontic Solution
Digitize, assess, and act on risk without leaving the Ontic Platform
Ontic puts security risk assessments, vulnerability management, and reporting into one connected workflow so you can spot issues, prioritize what matters, and track every step to resolution.
Platform
Centralize your data, cut the busywork, and get full context in one place.
Client Stories
Trusted by the people you trust
Trusted by thousands of security professionals at hundreds of leading brands. Ask around — chances are someone in your network already uses Ontic for risk assessments and mitigation.
Frequently Asked Questions
Risk Assessment Software FAQ
Ontic is compliant with the highest security standards, trusted by leading security teams, and ready to handle what your program demands.
Ontic has Federal Risk and Authorization Management Program (FedRAMP) “In Process” status and is listed on the FedRAMP Marketplace.
Risk and Vulnerability Assessment Resources