Accidental silos are holding you back
Accidental silos are holding you back
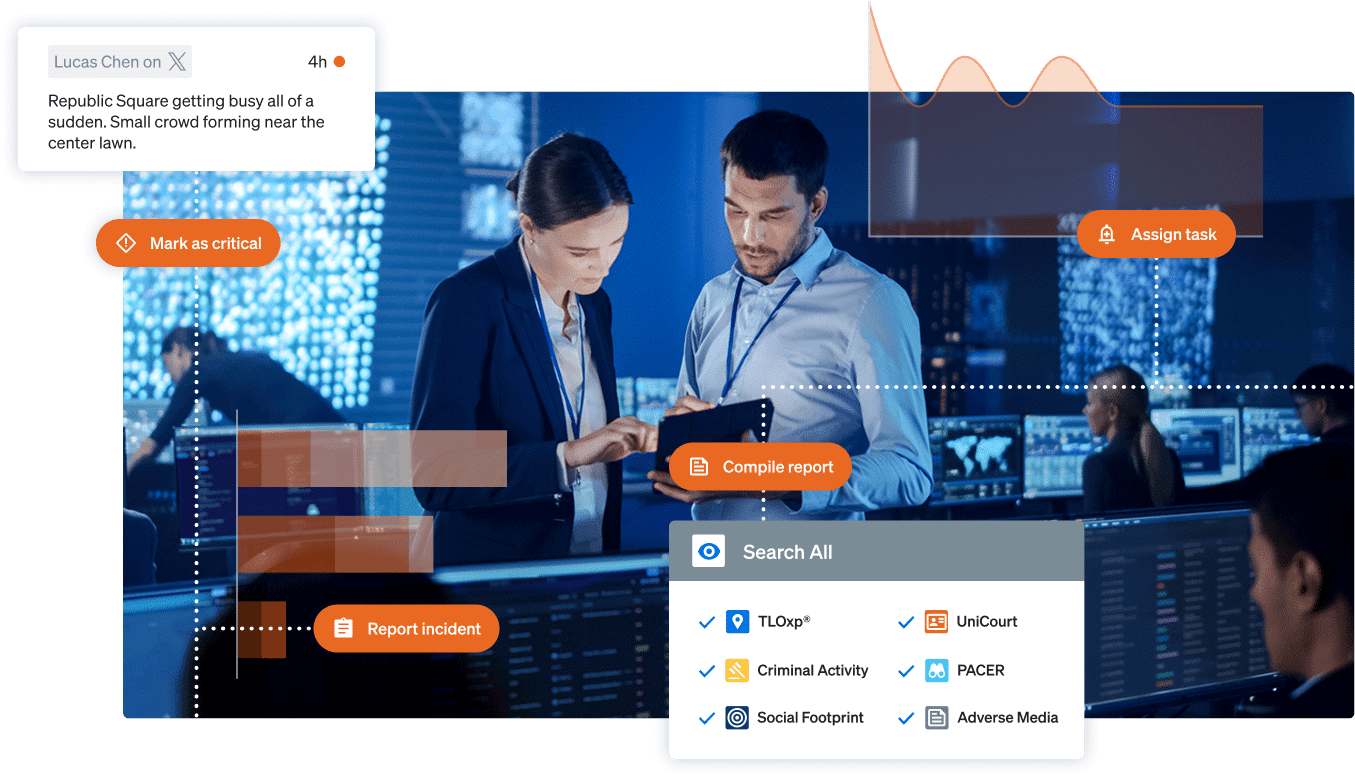
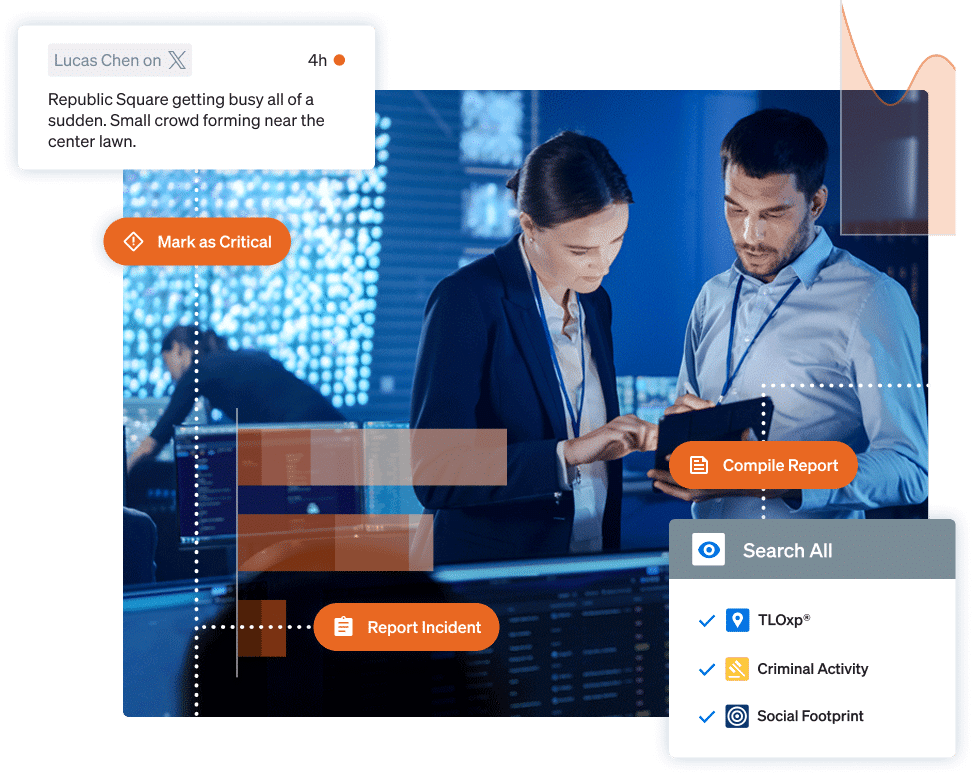
You didn’t set out to build silos. But as security tools multiply and data grows, disconnect creeps in. Signals get buried. Teams stay isolated. And security gets stuck in reactive mode.
We call these accidental silos — the hidden drag on your operation.
Connected Intelligence transforms your operation
Connected Data
Ditch the accidental silos
Bring all your data into one trusted system of record — so your team sees the full picture and acts with confidence.
Streamlined Operations
Eliminate the operational drag
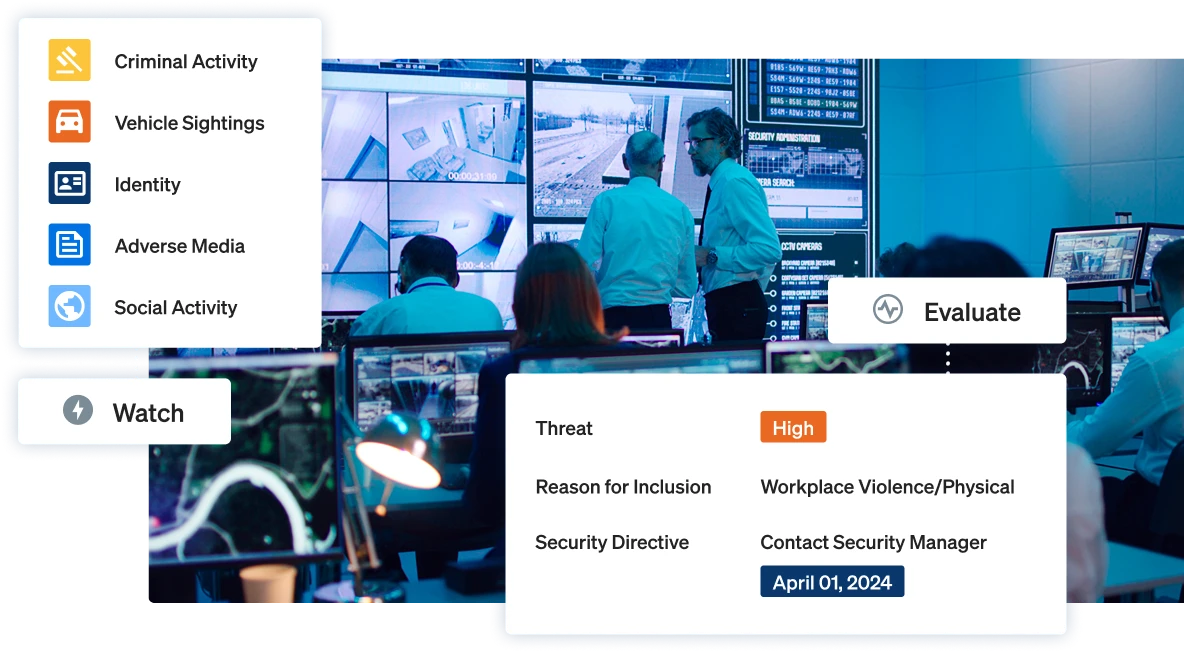
Automate the busywork, connect workflows, and give your team time back to focus on what really matters.
Strategic Foresight
End the reactive scramble
Shift from reacting to anticipating — and help your business make better decisions.
Programs We Serve
Tailored corporate security solutions for every program
Ontic Products
One physical security platform.
Multiple capabilities. Better security.
Ontic gives you a unified data foundation and advanced capabilities to operate with confidence — and future-proof your physical security management.
Ontic Platform
Govern corporate security from a single, secure system. Centralize data, automate workflows, improve collaboration — and deliver the insights that prove security’s impact.
Client Stories
Trusted by industry leaders
From Fortune 500 companies to federal agencies, Ontic helps security teams lead more strategic programs.
Ontic is compliant with the highest security standards, trusted by leading security teams, and ready to handle what your program demands.
Ontic has Federal Risk and Authorization Management Program (FedRAMP) “In Process” status and is listed on the FedRAMP Marketplace.
Built by experts.
Trusted by security leaders.
We’re more than software — our team of security experts and engineers delivers Connected Intelligence, combining human insight and technology to help you work smarter and move faster.
Get Security Tips Sent Directly to Your Inbox
Join 20,000+ security professionals