Physical and Digital Executive Protection: Synchronizing Domains
Exploring the relationship between executive cyber protection and physical security teams and some strategies to achieve these goals.
Organizations of all sizes continue to face risks from multiple vectors in the digital and physical domains. These domains overlap, and for at least half a decade, organizations have quietly discussed ways to converge these functions. The lack of unification for physical and digital executive protection has real effects on a majority of companies.
In Ontic’s 2022 State of Protective Intelligence Report, 84% of respondents said that “a lack of unified digital protective intelligence has in the past year resulted in missed threats and harm in companies.”
A unified effort between cybersecurity and physical security spheres will strengthen the ability of the risk enterprise to detect, deter, disrupt, and defend against hazards that can present a clear and present danger to life safety, networks and brands. That’s why I think convergence of physical and digital protection for executives will become more commonplace: when organizations unify intelligence functions, they enable resource sharing, amalgamate risk information and produce common operating information from which leadership can make decisions.
With this in mind, I want to go over some of the drivers of convergence, a few areas of mutual interest between executive cyber protection and physical protection teams and some strategies for achieving these goals.
Drivers of Convergence
The strain of a multi-year pandemic, the near-demonization of opponents in political discourse, and responses to the recent Russian invasion of Ukraine continue to tax organizations that were already managing a myriad of threat vectors under ‘normal’ circumstances.
In particular, the C-Suite has faced an increase in both physical and digital threats this past 24 months, fueled by issues stemming from (but not limited to) COVID-19. In 2020 sixty-nine percent of executives have seen a dramatic increase in physical threat activity against their companies. Likewise, the 2019 Verizon Data Breach Investigations Report (DBIR) also suggested corporate executives are 12 times more likely to be the target of social engineering attacks like phishing attempts. These trends have continued throughout the pandemic, with Verizon’s DBIR 2021 report describing increases in cyber-attacks across multiple vectors.
Alongside the rise in threats, digital and physical security teams find themselves in a state of telemetry overload. Navigating the haystacks of information requires security teams to remain fluid in both proactive and reactive activity. It is imperative to ensure all blue-hat actions are synchronized and coordinated. Doing so means adopting a unified framework of risk definitions, ratings, and operational categories to reduce noise, error, and resource blind spots.
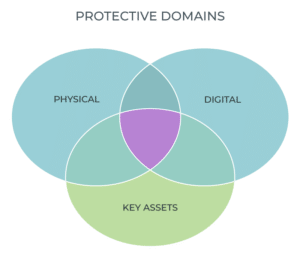
Common Operating Perspective
A 2019 study suggested that most firms spend between 0.2% to 0.9% of company revenue on cyber security for executive protection and other employees. A report by Genetec suggests that 84% of 1000 corporate physical security teams expect to remain flat or decrease in budget. While the digital executive protection team may be focused on change indicators, the physical defender could be focused on more geo-fixated events. Both are concerned about time/place/space, utilizing open-source intelligence (OSINT) resources, and maintaining platforms to do so. These tools and monitoring protocols can often be adjusted to support multiple needs and conserve resources in monetary and human costs.
Establishing a common understanding regarding “what’s important” is actually important in protecting senior leaders, high-value assets and organizational health. Failure to understand high-level monitoring criteria leaves critical gaps that bad actors can exploit. Intelligence can generally be bucketed into four areas: Strategic, which provides a high-level overview and insights regarding impacts; Operational, which focuses on emerging issues; Tactical, which leverages detailed information and insights around time and space; and the Technical, which covers specific, short term, information on ‘how’ adversaries might be working.
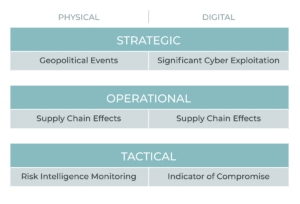
Where Digital and Physical Can Work Together
Working together regarding risk monitoring and mitigation will yield far stronger results, where joint activity is warranted. Chiefly the following areas are of biggest concern when creating an executive protection solution and present the greatest collective working opportunity and an excellent place to start any converged conversations:
Travel Security: Executives and employees present a great deal of risk while on travel. An amazing amount of risk ratings exist and are utilized within the enterprise. Combining information on alert and risk levels is important and will inform the company as to security postures both digitally and physically – reducing noise.
Monitoring: The daily task of maintaining overwatch over threats, both existing and/or burgeoning, to inform or protect the enterprise is daunting. Joint engagement regarding Priority Information Requirements (PRI) allows for streamlined resources (both human and application-based). While clearly there exist lines between both, having an understanding of what peer groups are focused on is helpful.
Communication: Where applicable, combined reporting to the C-suite underscores both a unified front on risk management and reduces noise to executives. Collective reporting allows for anticipating questions and responses, making way for the ability to be more thoughtfully reactive and, where possible, forecast potential problem spots.
Executive Risk Assessments: Evaluating the environments that executives work in is a basic function of both physical and digital executive protection efforts. While the physical protector examines risks to solidifying structures and escapes, the digital defender scans the network and cyber atmospherics for gaps at endpoints. Between both, the technical counter surveillance measures (TCSM) environment exists, assessing unwanted signal access. Unified working efforts reduce impacts on the executive’s schedules.
A Unified Team’s Role
Different groups all have their own focus points, but the goal of a converged team is to manage an “all-risk” profile, one that is aligned with the broadest goals of the enterprise. Be it customer-facing or an enterprise-level response, managing security and reaction requires many players to mitigate risks. Ensuring the safety and executive protection efforts are aligned within the individual scopes of defense effort is key to their work.
Therefore, the function of the team is to synchronize efforts, ensuring clear lines of communication exist between stakeholders and helping drive common operating information across all domains, with limited mandated authority but a directive to secure the executive levels of the corporation.
Next Steps
What can be done to establish an environment of mutually supportive work and not require a major shift in activity or thinking? To help you answer that question, I present you with a high-level checklist of the next steps to foster:
Define Key Risk Scenarios
01
Determine critical situations for each side and convergence points
Establishing Intelligence Requirements
01
Discuss joint collection activities
02
Define shared triggers and indicators, and the cross org alert process
03
Align SOCs in Support and Monitoring Protocols
Align Country Risk Definitions and Procedures
01
Merge ‘country risk’ levels holistically
02
Create one document aligned to enterprise threat levels