The Delivery Man Ruse: An Effective Method to Kill

Key Points
- If you want to prevent the next attack, understanding the “how” can be much more important than the “why”
- With numerous individuals to protect, technology can help prioritize resources
- Technology and threat assessments can help fill intelligence gaps
After a lifetime of examining attacks and failed plots, my eye has always been drawn to the “how” of the attack, rather than the “why”. Don’t get me wrong — the “why” is important for analysts and prosecutors, but not so much for the protectors or those charged with stopping the attack before it occurs. Why is that? Because if you can understand how an attack has been put together and what factors made it possible, you can do something to mitigate that threat going forward. This is one of the basic tenets of any protective intelligence investigation or after-action study: figure out the “how”. Frankly, it’s the only way you can stop an attack from occurring. Federal protective agencies like the U.S. Secret Service and the Department of State’s Diplomatic Security Service have learned this lesson the hard way over the years.
One tactic I’ve seen several times over the years is known as the “delivery man ruse”. Sadly, we saw this tactic employed successfully again on July 19th at the New Jersey home of a U.S. Federal Judge. In this case, the attacker disguised himself as a FedEx delivery man and was reportedly carrying a FedEx package when he arrived at the door. The attacker opened fire on the judge’s husband and her 20-year old son. Her son died of injuries sustained during the attack and her husband was critically injured.
I first considered this specific ruse in 1975 in reading James Grady’s brilliant thriller-turned-film called “Three Days of The Condor”, starring Robert Redford and Faye Dunaway. I’ve had the privilege of knowing and speaking to Jim for a podcast and his insights are fantastic. I saw the tactic used in real life in 1980 while I was on the scene of a transnational act of terror as a young EMT with the Bethesda-Chevy Chase Rescue Squad. The gunman — disguised as a mailman and using a stolen U.S. Postal Service jeep — shot and killed an Iranian dissident at his front door. I would later hunt for that killer as a special agent but we were too late — now he’s hunkered down and safehaved inside Iran. I suspect he may have gotten the idea for the ruse by watching the Hollywood film or reading Grady’s book.
In the latest case in New Jersey, the shooter (who we will not name) was a lawyer who had previously appeared before the judge he targeted. According to information found after the attack, the shooter died of a self-inflicted gunshot wound. He was fixated on revenge and had a targeted kill list. It later became clear that he had also killed before, murdering an attorney in California a few weeks earlier. He was a poster child for madness.
As threat hunters, our challenge is finding these stalkers and killers before they strike, but let’s first examine the challenges the protectors and analysts faced in this situation.
According to the U.S. Marshals service, the Judicial Security division is responsible for protecting about 2,700 judges and another 30,000 federal prosecutors and other court officials. From a practical perspective, there are simply not enough deputy U.S. Marshals to protect that many officials from known threats. The challenge for any protection team is figuring out how to separate the signals from the noise. Out of the potential range of threat actors, who poses the most serious risk? How do you evaluate and update your files? Where are your intelligence gaps? The other challenge is proximity of the threat actor to the potential target.
In our mobile world, distance can be covered quickly and fixated individuals can often act impulsively. Meanwhile, managing and keeping track of hundreds — if not thousands — of potential persons of interest or concern (known as POI’s) is daunting for any protection organization. Protectors need an alerting mechanism that can proactively highlight changes in behavior. A systematic, repeatable process combined with technology solutions that help sift through the noise of all of the information that’s available can help protectors keep track of threat actors, making it possible to delineate between a howler and a hunter. Easy-to-use behavioral threat assessment tools like WAVR-21 and SIGMA can give you an edge in threat assessment and prioritization.
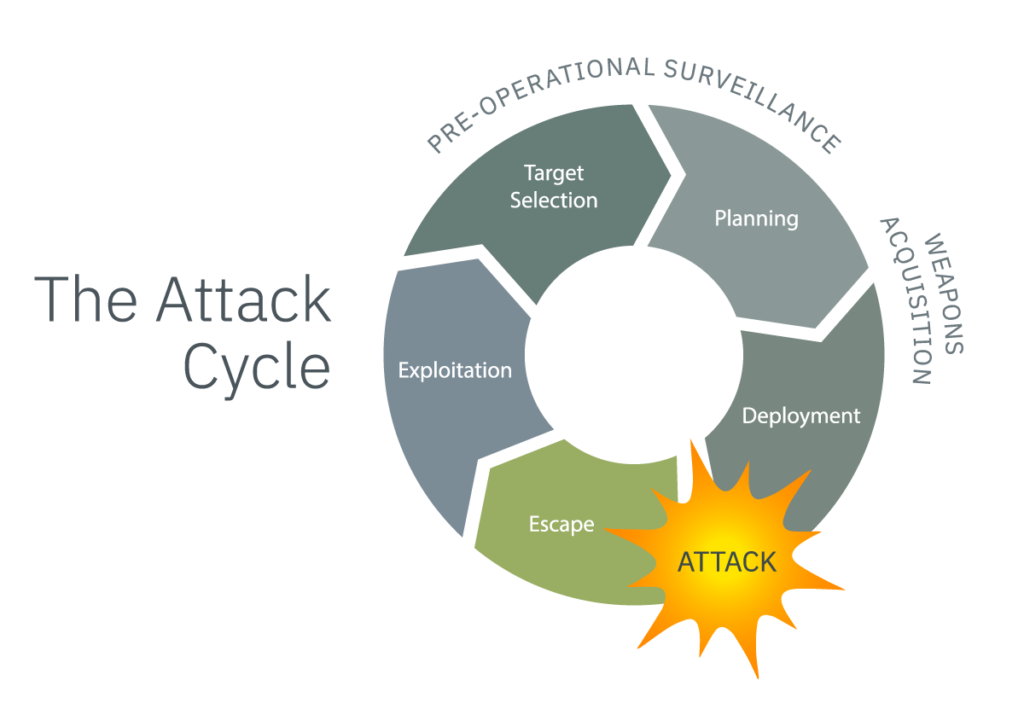
In reality, it has been my experience that unless you can interrupt the attack cycle — and EVERY attack has one — you can’t stop the attack, once the shooter turns operational, e.g., gets in his/her vehicle, turns the key and is on the way to the target. At this point, your only solutions are physical security barriers — even though most can be defeated — along with an overwhelming police response to neutralize the threat. With most attacks lasting a short few minutes, or even just a few seconds, the shooter often has the upper hand.
If I were back in the saddle in an official capacity in this case, I would start by asking several questions: How long was the victim under surveillance? How was the surveillance conducted? In order to find the pre-operational surveillance, you have to be looking for it. What were the signals?
Hindsight is always 20/20, but with the right tools, it’s often possible to detect and prevent these violent actions before they become tragic. Having the right team and the support of the right technology can greatly assist in triaging threats.



