Establishing a Proper Employee Termination Procedure to Mitigate Insider Threats

It’s not uncommon for companies to be overwhelmed when it comes to managing threats posed by separated employees. Once a terminated employee has left a company, many believe the potential threat has been removed from the workplace.
However, a successful employee termination procedure – one that avoids risks posed by insider threats – is actually more complex than many people think. From the employee who stole intellectual property to the terminated individual who committed an act of violence or abuse against former colleagues, insider threats are real and come in many different forms.
Insider Threats are a Company’s Greatest Risk
A great deal of research has been conducted over the years as it relates to insider threat awareness and workplace violence prevention. Four main types of individuals have been defined that can cause significant damage to a business, its brand, and its infrastructure.
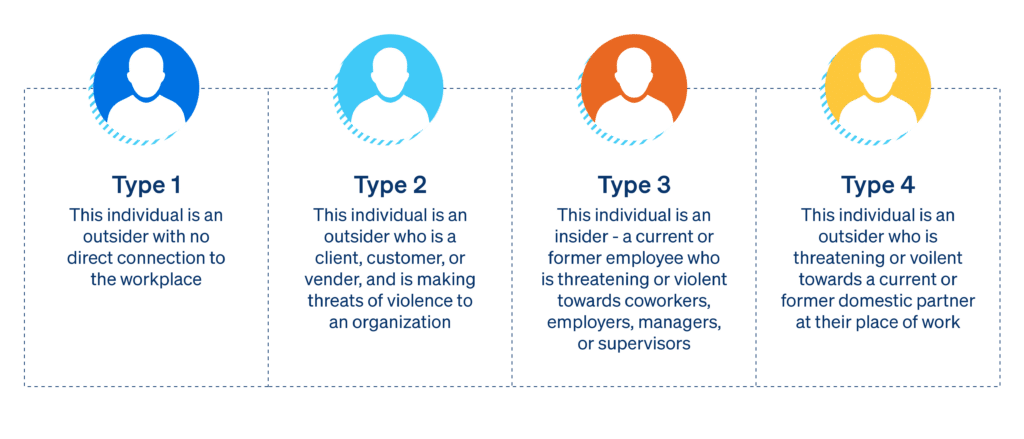
Source: Threat Assessment and Management Strategies – Identifying the Howlers and Hunters
While all of these potential threat actors should be taken into account, the type 3 individual is especially important – these individuals are typically the hardest to detect and the most likely to cause tremendous damage to a company & its people.
Current and former employees have deeper inside knowledge of the company, its people, as well as policies and protocols. This is what sets aside the type 3 individuals from other types – they have access to valuable information that outsiders lack. For this reason, companies need to implement a comprehensive employee termination procedure to help minimize resentment, so that an employee thinks twice before carrying out a malicious act against their previous employer.
By working with human resources and legal teams, security teams can develop advanced employee termination security procedures to protect their organization – legally, physically and technologically. Even more, they don’t end up with a former employee making threats or holding grievances. By creating a truly holistic termination process, workplace threats can be managed more objectively.
The Proper Procedure for Terminating an Employee
There are several considerations employers should take into account during the employee offboarding process. In general, the employee termination procedure should be thoughtful, respectful, and protect an individual’s dignity so separated employees will feel less resentment and will be less likely to pose an imminent threat to a company. Here are some additional measures to take into account:
- Detect anomalies in behavior prior to separation: Prior to the offboarding process, employers should enable automated activity monitoring to detect anomalies including suspicious login times, attempts to retrieve IP from a network, and attempts to extract data, among others.
- Organization-wide effort: Security measures when terminating an employee should stretch across the entire organization.
- Managers and human resources should be responsible for conducting exit interviews, providing final performance feedback, verifying time logs, and sending final paychecks.
- HR should finalize termination paperwork and be careful communicating termination to other employees in a way that avoids embarrassment.
- The finance department should ensure that the terminated employee does not have access to company credit cards or other financial accounts. It is recommended that either finance closes accounts and creates new ones or changes account information if an employee has access to numbers or passwords.
- Lastly, IT and security teams need to terminate all access to company accounts including email, communication channels, cloud services, applications, access points and others. They are also responsible for ensuring that the terminated employee returns all of their work equipment (laptops, monitors, authentication devices, badge cards, desk keys, parking passes, etc.) as well as any physical sensitive information.
- Privacy and discretion for the exit: While the employee termination process should be all-encompassing, only one or two individuals (e.g., frontline manager and HR) should be involved in conducting the termination. The termination meeting should be conducted in a place that is safe, to avoid any potential hazards.
- Structure of exit conversation: The individuals delivering the news should prepare a script for terminating an employee that includes concrete pieces of information such as the date of termination, the final paycheck, a review of NDAs and the key reasons for why the individual was let go. The second part should be more positive and future focused – opening the conversation up to any questions or concerns the terminated employee may have as well as a provided list of support resources. By prepping and planning what to say when terminating an employee, separated users can more easily understand the reasons for why they were terminated and next steps.
Sources: Software Engineering Institute, Employee Termination Procedure, Part 20. and Insider Threat Mitigation Guide
Next Steps & Continuous Monitoring
It doesn’t end there – organizations should remain proactive after an employee is terminated. In addition, employers should consider the acronym JACA, for identifying when violence is most likely to occur after an employee is terminated (Source: The Gift of Fear; Chapter 9: Occupational Hazards). Every so often, a separated employee may internally justify acts of violence if they believe that their employer has taken everything away from him/her. They may consider acts of violence because there is no other alternative, or they do not care about the consequences, or perhaps the separated employee may overestimate their ability to commit an act of violence.
Grievances, embarrassment, and disappointment may persist after an employee is terminated. When an individual feels ostracized, they may use their former knowledge to regain access to the company and its assets and even engage in malicious activity. Examples include exfiltrating data for one’s own advantage, selling trade secrets, leaking personal information (coworkers or customers), or simply using illegitimate access to physically harm an asset. Take the recent workplace violence incident at a Kroger in Collierville, Tennessee, for example, when a fired contractor walked back into the store, shooting 15 people and killing one. Or a Florida woman who hacked into her previous employer, a flight school, and cleared planes in for maintenance to fly.
However, there are ways that employers can avoid these types of situations from happening. Where possible, monitoring relevant social media and maintaining alerts in relation to the company may be necessary for a period of time. Any mentions of a fired employee making threats should be taken into serious consideration as well as any other news around the individual, such as recent arrests and/or criminal charges.
By creating a proper employee termination procedure that includes all relevant individuals, as well as enabling social monitoring after terminations, organizations can mitigate insider threats and avoid potential workplace violence. When separated employees have an understanding of employment termination, they are less likely to hold onto grievances. In addition, when all of the proper logistical steps are taken, such as wiping access to accounts and retrieving work equipment, companies can better protect data and other sensitive information. Lastly, when organizations take additional protective measures, they become aware of any anomaly or threat, thus reducing the likelihood of a malicious attack.






